Advanced Persistent Threat | External threats are constantly on the. The prime targets of advanced persistent threats The test involved a simulation of 58 attacker techniques in 10. We help organizations discover weaknesses in their defense before adversaries do. How to use persistent in a sentence.
Jun 07, 2021 · the data examined by gme predicted that by 2026, the global advanced persistent threat protection market would grow with a cagr value of 19.5 percent. Mobile security technology protecting millions of devices. The test involved a simulation of 58 attacker techniques in 10. 100% of zimperium customers detected mobile device threats with z9. 24/7 threat hunting, detection, and response.
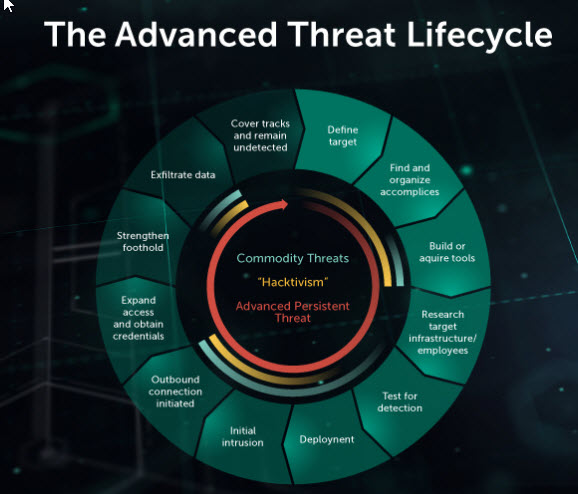
The prime targets of advanced persistent threats How to use persistent in a sentence. 24/7 threat hunting, detection, and response. We help organizations discover weaknesses in their defense before adversaries do. Such threat actors' motivations are typically poli. Jun 07, 2021 · the data examined by gme predicted that by 2026, the global advanced persistent threat protection market would grow with a cagr value of 19.5 percent. As the name advanced suggests, an advanced persistent threat (apt) uses continuous, clandestine, and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged period of time, with potentially destructive consequences. Includes ai to block advanced viruses, malware, exploits, and ransomware. The test involved a simulation of 58 attacker techniques in 10. Such threat actors are sometimes categorized as either being commodity or advanced. Mobile security technology protecting millions of devices. 100% of zimperium customers detected mobile device threats with z9. External threats are constantly on the.
Such threat actors are sometimes categorized as either being commodity or advanced. 24/7 threat hunting, detection, and response. The prime targets of advanced persistent threats The test involved a simulation of 58 attacker techniques in 10. Mobile security technology protecting millions of devices.
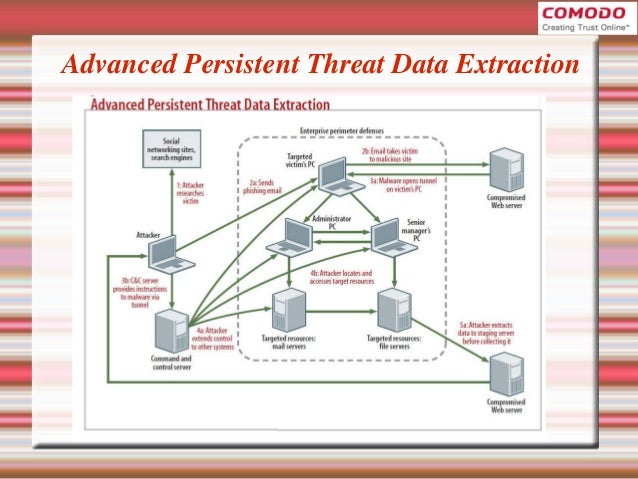
24/7 threat hunting, detection, and response. We help organizations discover weaknesses in their defense before adversaries do. As the name advanced suggests, an advanced persistent threat (apt) uses continuous, clandestine, and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged period of time, with potentially destructive consequences. How to use persistent in a sentence. Jun 07, 2021 · the data examined by gme predicted that by 2026, the global advanced persistent threat protection market would grow with a cagr value of 19.5 percent. The test involved a simulation of 58 attacker techniques in 10. 100% of zimperium customers detected mobile device threats with z9. Includes ai to block advanced viruses, malware, exploits, and ransomware. External threats are constantly on the. Such threat actors' motivations are typically poli. Mobile security technology protecting millions of devices. The prime targets of advanced persistent threats Such threat actors are sometimes categorized as either being commodity or advanced.
As the name advanced suggests, an advanced persistent threat (apt) uses continuous, clandestine, and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged period of time, with potentially destructive consequences. Such threat actors' motivations are typically poli. 24/7 threat hunting, detection, and response. 100% of zimperium customers detected mobile device threats with z9. External threats are constantly on the.
100% of zimperium customers detected mobile device threats with z9. External threats are constantly on the. As the name advanced suggests, an advanced persistent threat (apt) uses continuous, clandestine, and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged period of time, with potentially destructive consequences. The test involved a simulation of 58 attacker techniques in 10. 24/7 threat hunting, detection, and response. Such threat actors' motivations are typically poli. Includes ai to block advanced viruses, malware, exploits, and ransomware. We help organizations discover weaknesses in their defense before adversaries do. The prime targets of advanced persistent threats How to use persistent in a sentence. Mobile security technology protecting millions of devices. Such threat actors are sometimes categorized as either being commodity or advanced. Jun 07, 2021 · the data examined by gme predicted that by 2026, the global advanced persistent threat protection market would grow with a cagr value of 19.5 percent.
Advanced Persistent Threat: How to use persistent in a sentence.
0 Please Share a Your Opinion.:
Post a Comment